Tighten SSH access to your cloud resources using short-lived SSH certificates

SSH access using public private key based authentication has several drawbacks that could potentially compromise your organization’s SSH access security. SSH certificate based authentication is a great alternative that addresses most of these security problems.

SSH Communications Security Introduces Access Management at the
Configuring and using the appliance
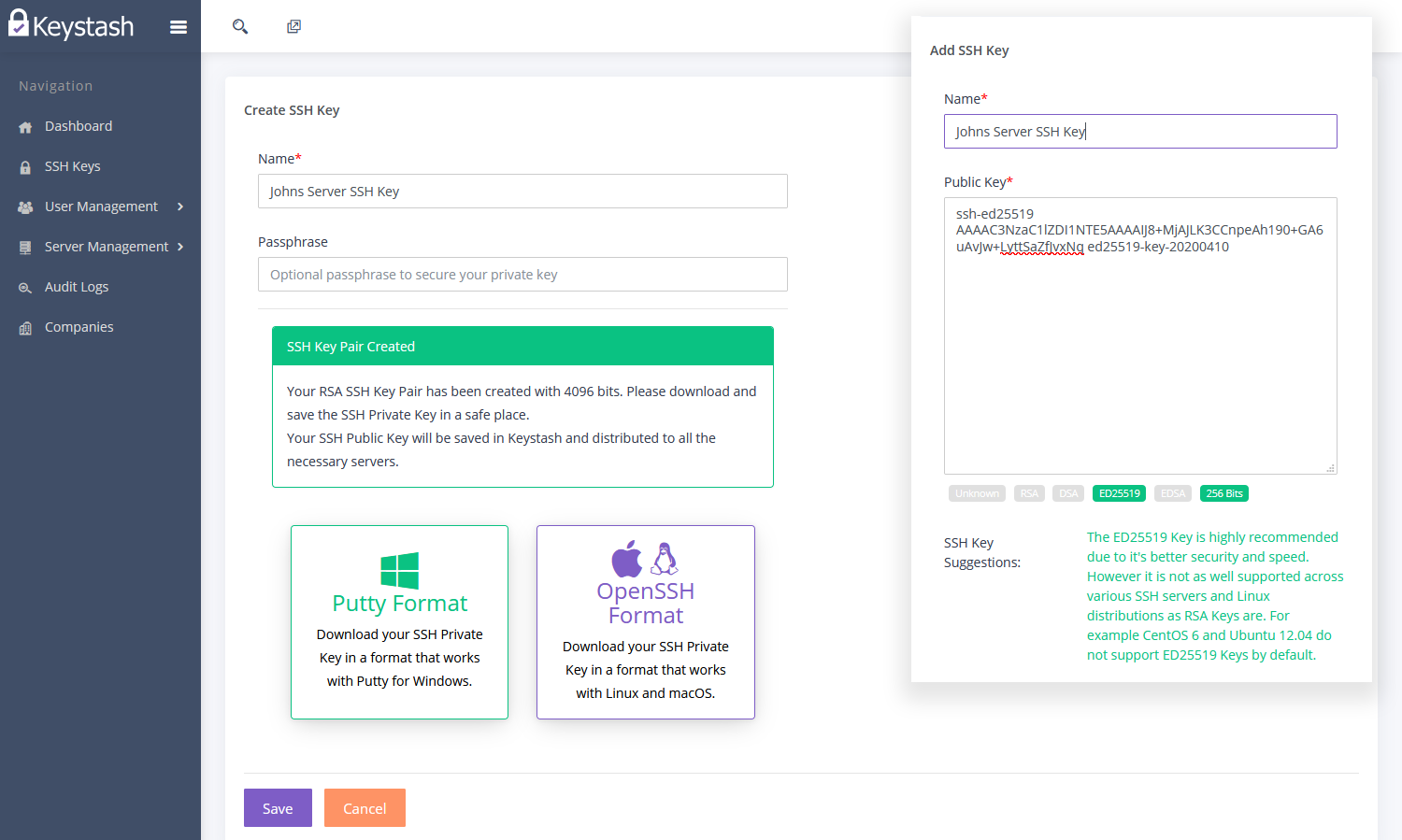
Keystash Linux SSH Key Management Software
How to fix SSH errors - IONOS
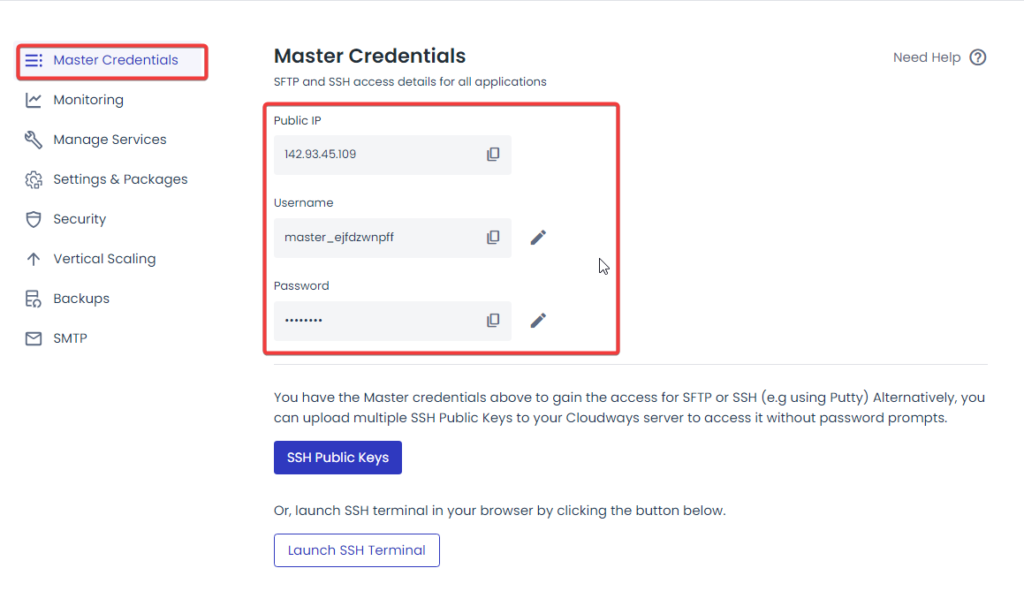
How to Host WordPress on Hosting EC2
Automation of Lets Encrypt certificate updates
SSH key management best practices: Beyond SSH Keys

SSH certificates for secure authentication

The 6 Pillars of Platform Engineering: Part 1 — Security - The New
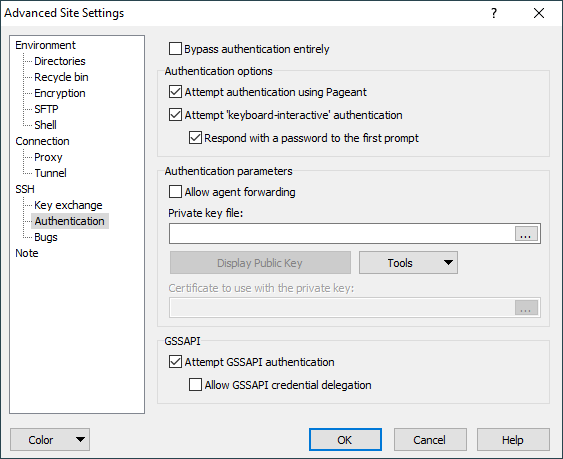
The Authentication Page (Advanced Site Settings dialog) :: WinSCP

SSH Key Management Overview & 10 Best Practices

Sensors, Free Full-Text
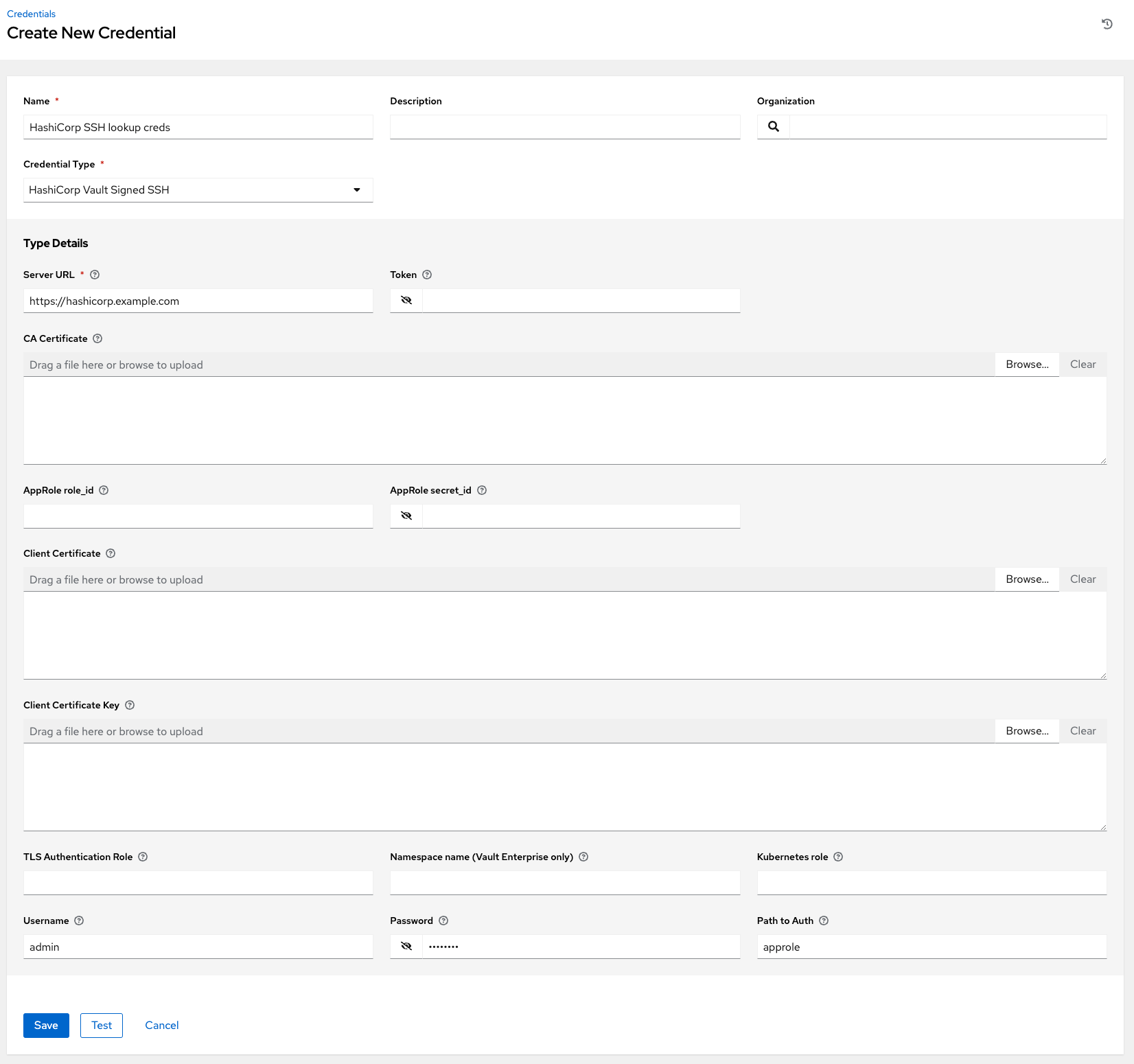
Automation Controller User Guide Red Hat Ansible Automation